A short introduction to MiTM attack and its possible progression
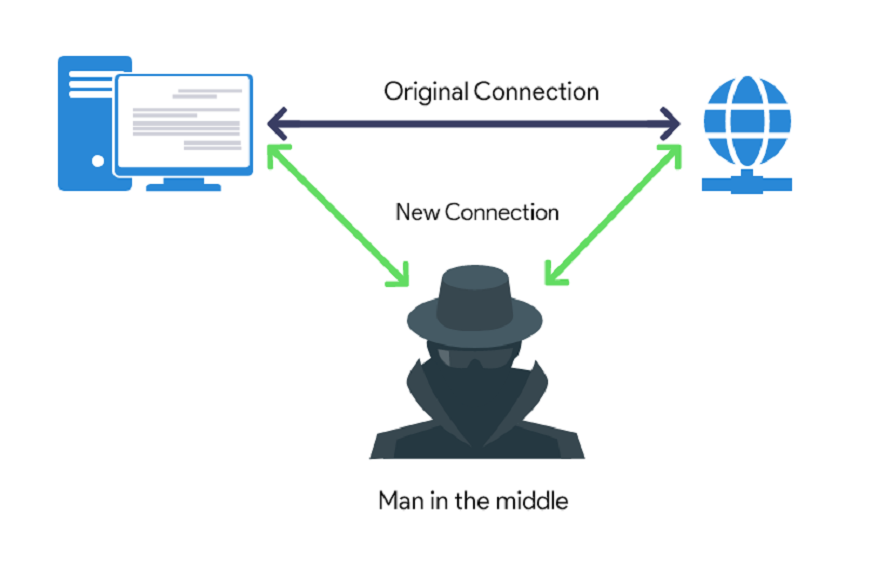
A man-in-the-middle (MITM) attack happens when a perpetrator introduces himself into communication between a user and an application, either to monitor or counterfeit one of the parties, making it appear as if a normal information exchange occurs.
MiTM attack is equivalent to eavesdropping but the attacks do not end at the breach of confidentiality. The content of these conversations changes the request through the parameters as well as the results that are returned by the server. It means the attacker holds the potential to modify the user interface.
There are many security analysts who find it difficult to perform the MiTM testing to assess the mobile app security. In order to excel the process, it is first often used in intercepting the app network traffic and then using it to ease the activities of the attackers.
When apps accept legitimate CA certs with an incorrect hostname, hostname verification issues can arise. Attackers can easily eavesdrop on the network traffic. It could be done using the certificate for the domain that hardly matches with the endpoints they are actuallyusing.
While using the mobile app, MiTM attacks stem from the app client-side issues by resulting from the barcode that are displayed. The scenario requires to be tackled with prosperity. Intercepting of the mobile app networking traffic is to be monitored well so that attackers cannot get through easily.
Network traffic Interception is another key feature that gets the most intercepting information that is mandatory and at times seen to be unprotected in the network traffic. Basically Network issues happen on LTE networks mostly. It is over free virtual private network apps and many other scenarios. It is best to operate under the assumption which makes network are hostiles.
The main purpose of the attacker is to get through the personal data as well as information set with account information, credentials and credit cards so that they can steal by using the data. Those who use the financial apps also use the technology of the SaaS enterprises, e-commerce sites, and other websites. All that it requires is signing of the typical targets.
With the information gathered during an attack, identity theft, unapproved fund transfers, and unauthorized password changes could be possible.The other issue with MiTM is its lack of authentication. Appsealing is a trusted name which takes full care of each and every aspect quite affordably.
In a much wider aspect, a MiTM attack is equivalent to the activities of a mailman who opens up your bank statement on the way. A fraud mailman will always write down the information and then resend the envelope by delivering the information to the door of the real owner. And, the owner remained unaware and ignorant of the fact that all his or her information has been stolen.
Man-in-the-middle includes as a connectivity between web apps and the main user. Thus it needs a special check and monitoring while you are using it. Successful MiTM execution holds 2 distinct phases. One is decryption and interception.






